고정 헤더 영역
상세 컨텐츠
본문
OpenCover is a free and open source code coverage tool for.NET 2 and above (Windows OSs only - no MONO), with support for 32 and 64 processes and covers both branch and sequence points. It uses the profiler API that is currently only available to.NET Frameworks running on the Windows platform.
De dust2 vmf download css syllabus. In the context of hardware and software systems, formal verification is the act of proving or disproving the correctness of intended algorithms underlying a system with respect to a certain formal specification or property, using formal methods of mathematics.[1]
Formal verification can be helpful in proving the correctness of systems such as: cryptographic protocols, combinational circuits, digital circuits with internal memory, and software expressed as source code.
The verification of these systems is done by providing a formal proof on an abstract mathematical model of the system, the correspondence between the mathematical model and the nature of the system being otherwise known by construction. Examples of mathematical objects often used to model systems are: finite state machines, labelled transition systems, Petri nets, vector addition systems, timed automata, hybrid automata, process algebra, formal semantics of programming languages such as operational semantics, denotational semantics, axiomatic semantics and Hoare logic.[2]
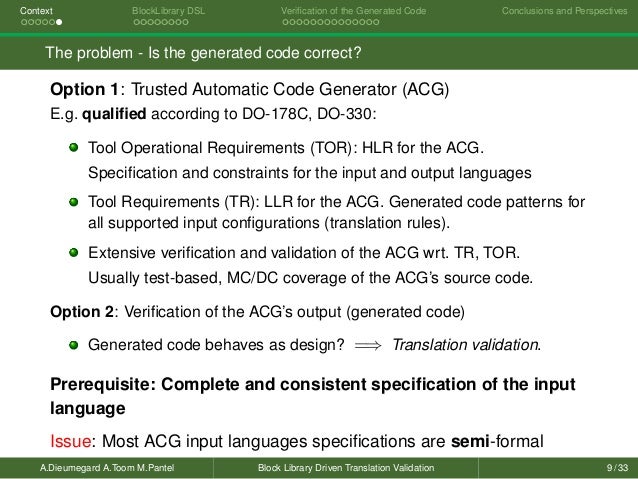
- 1Approaches
Approaches[edit]
One approach and formation is model checking, which consists of a systematically exhaustive exploration of the mathematical model (this is possible for finite models, but also for some infinite models where infinite sets of states can be effectively represented finitely by using abstraction or taking advantage of symmetry). Usually this consists of exploring all states and transitions in the model, by using smart and domain-specific abstraction techniques to consider whole groups of states in a single operation and reduce computing time. Implementation techniques include state space enumeration, symbolic state space enumeration, abstract interpretation, symbolic simulation, abstraction refinement.[citation needed] The properties to be verified are often described in temporal logics, such as linear temporal logic (LTL), Property Specification Language (PSL), SystemVerilog Assertions (SVA),[3] or computational tree logic (CTL). The great advantage of model checking is that it is often fully automatic; its primary disadvantage is that it does not in general scale to large systems; symbolic models are typically limited to a few hundred bits of state, while explicit state enumeration requires the state space being explored to be relatively small.
Source Code Validation Tools Download
Another approach is deductive verification. It consists of generating from the system and its specifications (and possibly other annotations) a collection of mathematical proof obligations, the truth of which imply conformance of the system to its specification, and discharging these obligations using either interactive theorem provers (such as HOL, ACL2, Isabelle, Coq or PVS), automatic theorem provers, or satisfiability modulo theories (SMT) solvers. This approach has the disadvantage that it typically requires the user to understand in detail why the system works correctly, and to convey this information to the verification system, either in the form of a sequence of theorems to be proved or in the form of specifications of system components (e.g. functions or procedures) and perhaps subcomponents (such as loops or data structures).
Software[edit]
Formal verification of software programs involves proving that a program satisfies a formal specification of its behavior. Subareas of formal verification include deductive verification (see above), abstract interpretation, automated theorem proving, type systems, and lightweight formal methods. A promising type-based verification approach is dependently typed programming, in which the types of functions include (at least part of) those functions' specifications, and type-checking the code establishes its correctness against those specifications. Fully featured dependently typed languages support deductive verification as a special case.
Another complementary approach is program derivation, in which efficient code is produced from functional specifications by a series of correctness-preserving steps. An example of this approach is the Bird–Meertens formalism, and this approach can be seen as another form of correctness by construction.
These techniques can be sound, meaning that the verified properties can be logically deduced from the semantics, or unsound, meaning that there is no such guarantee. A sound technique yields a result only once it has searched the entire space of possibilities. An example of an unsound technique is one that searches only a subset of the possibilities, for instance only integers up to a certain number, and give a 'good-enough' result. Techniques can also be decidable, meaning that their algorithmic implementations are guaranteed to terminate with an answer, or undecidable, meaning that they may never terminate. Because they are bounded, unsound techniques are often more likely to be decidable than sound ones.
Verification and validation[edit]
Verification is one aspect of testing a product's fitness for purpose. Validation is the complementary aspect. Often one refers to the overall checking process as V & V.
- Validation: 'Are we trying to make the right thing?', i.e., is the product specified to the user's actual needs?
- Verification: 'Have we made what we were trying to make?', i.e., does the product conform to the specifications?
The verification process consists of static/structural and dynamic/behavioral aspects. E.g., for a software product one can inspect the source code (static) and run against specific test cases (dynamic). Validation usually can be done only dynamically, i.e., the product is tested by putting it through typical and atypical usages ('Does it satisfactorily meet all use cases?').
MS Windows Vista Home Basic 32bit Serial number The serial number for MS is available This release was created for you, eager to use MS Windows Vista Home Basic 32bit full and with without limitations. Find great deals on eBay for Windows Vista Home Basic 32 Bit in Computer Operating Systems Software. Shop with confidence. Find great deals on eBay for Windows Vista Home Basic 32 Bit in Computer Operating Systems Software. Shop with confidence. Skip to main content. EBay: Shop by category. Shop by category. Seriales para windows vista home basic 32 bit.

Automated program repair[edit]
Program repair is performed with respect to an oracle, encompassing the desired functionality of the program which is used for validation of the generated fix. A simple example is a test-suite—the input/output pairs specify the functionality of the program. A variety of techniques are employed, most notably using satisfiability modulo theories (SMT) solvers,[4] and genetic programming,[5] using evolutionary computing to generate and evaluate possible candidates for fixes. The former method is deterministic, while the latter is randomized.
Program repair combines techniques from formal verification and program synthesis. Fault-localization techniques in formal verification are used to compute program points which might be possible bug-locations, which can be targeted by the synthesis modules. Repair systems often focus on a small pre-defined class of bugs in order to reduce the search space. Industrial use is limited owing to the computational cost of existing techniques.
Industry use[edit]
The growth in complexity of designs increases the importance of formal verification techniques in the hardware industry.[6][7] At present, formal verification is used by most or all leading hardware companies,[8] but its use in the software industry is still languishing.[citation needed] This could be attributed to the greater need in the hardware industry, where errors have greater commercial significance.[citation needed] Because of the potential subtle interactions between components, it is increasingly difficult to exercise a realistic set of possibilities by simulation. Important aspects of hardware design are amenable to automated proof methods, making formal verification easier to introduce and more productive.[9]
Serial Dilution: Importance and Aplication. Dilution is the act of mixing a chemical with other substance, usually distilled water to make it lighter in composition. Titration Medtalk The serial dilution of a substance of interest. Serial dilution involves repeatedly mixing known amounts of source culture with. Importance of serial dilution in serology crp. CRP rises within two hours of the onset of inflammation, up to a 5. Culture-negative infective endocarditis. The importance of serology to identify non. Tenfold serial dilution was done till reaching a concentration. C-reactive protein (CRP). C-reactive protein (CRP) detection that is of importance for. Its half- life of 1. A serial dilution is a series of sequential dilutions used to reduce a dense culture of cells to a more usable concentration. The easiest method is to make a series of 1 in 10 dilutions.
It's easy to import your existing products into your CS-Cart web store using simple import wizards. Cs-cart free download crack. You can import orders, products, categories, images, category relationships and more from a CSV file. If the stock for some product is below the defined threshold, your sales dept is notified by email.
As of 2011, several operating systems have been formally verified:NICTA's Secure Embedded L4 microkernel, sold commercially as seL4 by OK Labs;[10] OSEK/VDX based real-time operating system ORIENTAIS by East China Normal University;[citation needed] Green Hills Software's Integrity operating system;[citation needed] and SYSGO's PikeOS.[11][12]
As of 2016, Yale and Columbia professors Zhong Shao and Ronghui Gu developed a formal verification protocol for blockchain called CertiKOS.[13] The program is the first example of formal verification in the blockchain world, and an example of formal verification being used explicitly as a security program.[14]
As of 2017, formal verification has been applied to the design of large computer networks[15] through a mathematical model of the network,[16] and as part of a new network technology category, intent-based networking.[17] Network software vendors that offer formal verification solutions include Cisco[18] Forward Networks[19][20] and Veriflow Systems.[21]
The CompCert C compiler is a formally verified C compiler implementing the majority of ISO C.
Javascript Code Validation Tool
See also[edit]
Free Validation Codes
| Look up verifiability in Wiktionary, the free dictionary. |
References[edit]
Css Validation Tool
- ^Sanghavi, Alok (May 21, 2010). 'What is formal verification?'. EE Times Asia.
- ^Introduction to Formal Verification, Berkeley University of California, Retrieved November 6, 2013
- ^Cohen, Ben; Venkataramanan, Srinivasan; Kumari, Ajeetha; Piper, Lisa (2015). SystemVerilog Assertions Handbook (4th ed.). CreateSpace Independent Publishing Platform. ISBN978-1518681448.
- ^Favio DeMarco; Jifeng Xuan; Daniel Le Berre; Martin Monperrus (2014). Automatic Repair of Buggy If Conditions and Missing Preconditions with SMT. Proceedings of the 6th International Workshop on Constraints in Software Testing, Verification, and Analysis (CSTVA 2014). pp. 30–39. arXiv:1404.3186. doi:10.1145/2593735.2593740. ISBN9781450328470.
- ^Le Goues, Claire; Nguyen, ThanhVu; Forrest, Stephanie; Weimer, Westley (January 2012). 'GenProg: A Generic Method for Automatic Software Repair'. IEEE Transactions on Software Engineering. 38 (1): 54–72. doi:10.1109/TSE.2011.104.
- ^Harrison, J. (2003). 'Formal verification at Intel'. 18th Annual IEEE Symposium of Logic in Computer Science, 2003. Proceedings. pp. 45–54. doi:10.1109/LICS.2003.1210044. ISBN978-0-7695-1884-8.
- ^Formal verification of a real-time hardware design. Portal.acm.org (June 27, 1983). Retrieved on April 30, 2011.
- ^'Formal Verification: An Essential Tool for Modern VLSI Design by Erik Seligman, Tom Schubert, and M V Achutha Kirankumar'. 2015.
- ^'Formal Verification in Industry'(PDF). Retrieved September 20, 2012.
- ^'Abstract Formal Specification of the seL4/ARMv6 API'(PDF). Archived from the original(PDF) on May 21, 2015. Retrieved May 19, 2015.
- ^Christoph Baumann, Bernhard Beckert, Holger Blasum, and Thorsten Bormer Ingredients of Operating System Correctness? Lessons Learned in the Formal Verification of PikeOS
- ^'Getting it Right' by Jack Ganssle
- ^Harris, Robin. 'Unhackable OS? CertiKOS enables creation of secure system kernels'. ZDNet. Retrieved June 10, 2019.
- ^'CertiKOS: Yale develops world's first hacker-resistant operating system'. International Business Times UK. November 15, 2016. Retrieved June 10, 2019.
- ^Heller, Brandon. 'Seeking truth in networking: from testing to verification'. Forward Networks. Retrieved February 12, 2018.
- ^Scroxton, Alex. 'For Cisco, intent-based networking heralds future tech demands'. Computer Weekly. Retrieved February 12, 2018.
- ^Lerner, Andrew. 'Intent-based networking'. Gartner. Retrieved February 12, 2018.
- ^Kerravala, Zeus. 'Cisco brings intent based networks to the data center'. NetworkWorld. Retrieved February 12, 2018.
- ^'Forward Networks: Accelerating and De-risking Network Operations'. Insights Success. Retrieved February 12, 2018.
- ^'Getting Grounded in Intent=based Networking'(PDF). NetworkWorld. Retrieved February 12, 2018.
- ^'Veriflow Systems'. Bloomberg. Retrieved February 12, 2018.




